The financial services industry is based on trust, and security breaches and non-compliance carry penalties and high reputational costs. Therefore, maintaining cybersecurity systems is imperative for banks, and it’s an increasingly difficult task in the digital age.
With an accelerating rate of change and ever more amounts of data in play, operational risk management – including security and compliance issues for retail banks – have grown considerably. Today’s banking leaders are faced with two somewhat opposing forces – the need to undergo digital transformation and the need to ensure the security of their systems.

False confidence
Given the stakes, it’s surprising that many bank executives report being less concerned about cybercrime than they were three years ago. According to a Cornerstone study, almost 50 percent of bank executives put cybersecurity at the top of their list of concerns in 2018. Fast forward to 2020, and that number has fallen to 21 percent.

Although this opinion data doesn’t fully reflect the impact of COVID-19, it shows that, in recent years, cybersecurity policy has become business as usual. Many banks now have better internal security practices, data protection officers and alert systems. However, there is still some level of complacency. And it’s unlikely that things will get easier from here.
The digitization of financial services continues. And the introduction of open banking has enabled a new set of possibilities, but it’s also opened the door to more potential vulnerabilities. Hackers are using artificial intelligence to increase the effectiveness of their attacks. Advanced persistent threats from state-level actors are an ongoing issue, and in addition many banks have yet to come to terms with the full security implications of cloud adoption. In response, we will examine three categories of cybersecurity challenges and discuss how banks can respond.
Cyber threats during COVID-19
Scammers like to prey on unexpected events or hardships, and the global pandemic has been no exception. With many people forced to work from home (WFH), bad actors have more opportunities to target weak remote access controls, new endpoint devices and naïve employees.
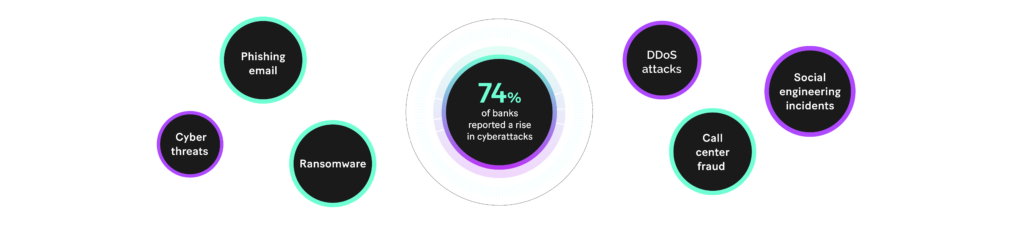
Since WFH became the default in 2020, 74 percent of banks reported a rise in cyberattacks. In addition, there has also been an uptick in phishing emails, DDoS attacks, call center fraud and social engineering incidents. Indeed, in the last year, cyber threats – from malicious domains to malware to ransomware – have increased across the board.
Solutions
Banks must adapt to a reality where employees operate outside the safety of their network fences. This means focusing on securing the endpoints, including laptops and mobile devices. It means using virtual desktop-server technology or virtual private networks (VPNs) to allow access to internal networks.
There’s also an equipment challenge, which means trying to get as much hardware with corporate malware protections, AV and local firewalls into employees’ hands as possible. Finally, many leading banks have also created educational initiatives to inform and remind staff about cyber-hygiene.
Issues around cloud adoption
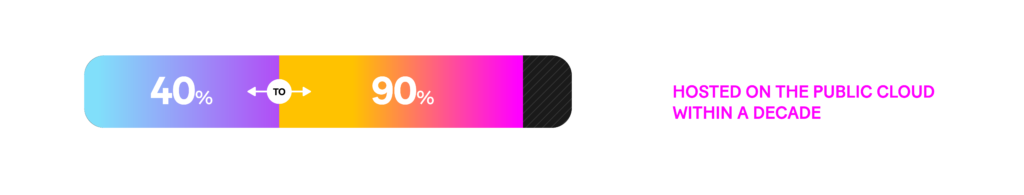
McKinsey estimates that 40 percent to 90 percent of banks‘ workloads will be hosted on the public cloud within a decade. Yet currently, security is the most commonly referenced barrier to adoption. Regarding cloud migration, the concern is trusting a third party to store data and handle security-sensitive operations. It can be difficult for financial institutions with multiple cloud networks to track where data is being stored and accessed.
And there’s also the issue of data sovereignty and (in some places) regulatory uncertainty. This and the consolidation of numerous organizations within one cloud service provider (CSP) create an extra appealing target for would-be criminals.
Solutions
First, it’s worth noting that trusting a cloud provider isn’t the risk it once was. Banks are increasingly coming around to the idea that big cloud providers, with their massive IT budgets, are likely the safest available option.
In terms of security-sensitive operations, these issues can largely be mitigated with proper due diligence – reviewing procedures and, as noted in a recent editorial, only selecting data centers that are PCI DSS approved and service providers that are PCI PIN approved. Beyond that, banks can (and should) develop a cloud cybersecurity task force to discuss new developments, key metrics and create security checklists and network monitoring plans.
Open banking and third-party providers
Research shows that 49 percent of bank customers believe their data will be less safe due to open banking. This fear is not unfounded, as data can be exposed not just in a direct attack on a banking app but also when an API used by an app is compromised.
In this sense, perpetrators often use brute force attacks or phishing targeted at individual API developers. Another way it often shows up is with credential abuse, where the hacker uses stolen login information to gain access to sensitive systems. According to one source, 75 percent of all such attacks against the financial services industry target APIs. And with open banking, the bank still assumes responsibility for any breach, so it’s essential that financial institutions monitor third-party risk properly.
Solutions
When it comes to open banking, what’s needed is a multilayered approach. Employing multi-factor authentication heads off a large percentage of potential problems, for instance. But it’s even better when combined with artificial intelligence (AI) and machine learning (ML) tools designed to monitor payments routed through open banking APIs in search of abnormal commands, transactions or other unusual activity.
From the start, Europe has been aware of the risks inherent in open banking. And it’s worth highlighting the fact that they have been carefully factored into PSD2. Indeed, this regulation imposes the use of strong customer authentication (SCA) when accessing bank data. It also requires the actors to be regulated and subjected to constraints.
European SCA practices should be exported to other markets to limit the risks around authentication. In the same way, making access to data conditional on a partner’s wrapping phase and securing access by technical means with authorized partners will further reduce these risks.
Final thoughts
Cybercriminals are constantly deploying new tactics, making it important for security teams to proactively build countermeasures before something happens. Despite major efforts to protect against a continual stream of ever-more sophisticated attacks, cyber risk management in the banking sector is no small task. At a minimum, banking leaders need to have an understanding and awareness of the various cyber threats they face.
Compliance with applicable regulations is the obvious first step towards protection. But, beyond that, financial institutions need to operate on the front foot, anticipating rather than reacting. This can be achieved via increased cooperation between banks and financial firms. Sharing notes on attacks and organizing simulations might not eliminate cyberattacks, but it can help build stronger defenses and significantly reduce response times.